Self Sovereign Identity can do just fine, blockchain-less
KERI, an open protocol for identifiers
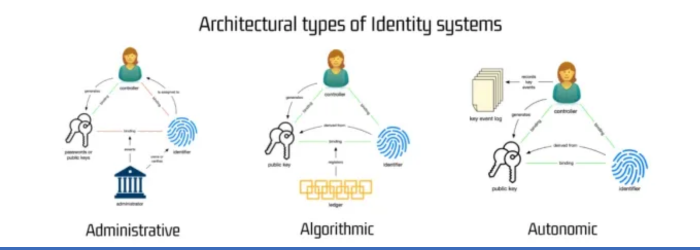
Source: https://www.windley.com/archives/2020/09/the_architecture_of_identity_systems.shtml
Example : Is the secret key of public key A compromised? Get the next public key B from your wallet and that way you use the next secret key for signing future documents. Future secret keys don’t have to be in the same place as the active device you’re currently using, or as Smith puts it, you can store all that in a safe in a mountain with an army of navy seals out front.
Because KERI identifiers and event logs are self-certifying, they can use any system as a witness, as long as the system in question can store and return data. So other key event logs, but also blockchains, traditional databases, file systems, etc. In this way, key event logs form signed hashed data structures that provide a verifiable key state.
Because everything relies on cryptographic links, KERI identifiers can be linked together in such a way that it is always provable who or what has ever verified an identifier or what permissions have been granted to an identifier. In this way, a government can be a reliable source for verifying an identity and a company can identify a person as authorized to sign. Or, conversely, revoke that authority. In this way it is possible to create an entire hierarchy of identifiers.
This works with the functions that KERI adds to identifiers, namely: inception, pre-rotation, rotation, delegation, and revocation. In addition, there are numerous derived and ancillary functions. Think of functions such as signing, committing (of data) that remain verifiable up to the source of the trust: the public-secret key pairs that the controller generated in his vault in his mountain, without having to trust intermediate parties.
So how does that work with, say, something like a personal identity, how do I prove it?
“Very simply, you create a verifiable link between a natural person and a cryptonymous identifier.”
And what does such a cryptonoumos identifier mean?
“Which is derived from your public-secret key pair in the beginning, but that identifier remains. So, you can rotate your keys, but you keep the same identifier. The key event log says, ‘here are the keys that control the identifier and no one else can create them.’ Then a reputable entity, the government for example, says, ‘I’m going to challenge you, natural person, to prove to me that you are the custodian of this identifier’. You can prove that by signing something with the secret key. I can verify that your signature can only come from the secret key if I have your public key, which proves that you have control over it. Then I, the government agency, will issue a certificate that says, “this is signed by the government’s crypto-anonymous identifier that is universally published so that everyone can verify that it is correct. Because the public identifier that you, the natural person with this name and personally identifiable information, is the controller of this crypto-anonymous identifier, this person is the controller of the secret keys.”
“We prefer to call it ‘autonomic identifier’ rather than crypto-anonymous, because that’s a bit easier to pronounce and better conveys the idea of self-governance. Self-governing because it is controlled by the custodian of the secret keys, not another entity. Yet for the purpose of determining the identity of you as a natural person, the reputable entity has made the connection with your identifier. This allows us to say, ‘okay, officially this identifier belongs to you, natural person’. So with that certificate, if you’re willing to show it, you can prove who you are. Or you can apply it in a privacy-protecting way in that you can prove through cryptographic links that you are, for example, old enough to buy liquor, but without having to give up anything about yourself. GLEIF does this not for natural persons, but for companies and institutions. And that makes pretty good sense: they sign a lot all day long.”
“Many people who know a lot about blockchains say: it can’t be done! Now my challenge is to explain that it can. So in the meantime, that’s gotten through to GLEIF , the Global Legal Entity Identifier Foundation, sort of the W3C for identifiers.”
How can I practically shape all that as an end user? What do I need?
“You need a device that can do cryptography, so something like a cell phone or other device with similar capabilities. In those devices there’s a secure enclave or something, that’s not such a problem.”
And what if I lose the lot? Backup?
“You need a backup of the secret keys, but that’s not a problem these days. A password manager, a hard copy backup, or mechanisms to share secrets. Since the advent of Bitcoin and many wallets, the options around backups have gotten better and better. But the importance of KERI is to be a good protocol, not to build a good user interface. That’s what others do.”
And what about people who can’t or no longer operate these kinds of systems themselves?
“Now that’s the beauty of delegation: if you build delegation into identity systems, then you can prove that someone is a guardian; the whole chain is verifiable.”
“But it’s interesting, you’re talking about usability now. That’s something that does get solved. The problem is: if you sacrifice security for usability, you lose trust.”
The latter, trust, is one of the Internet’s biggest problems, according to Smith: trust cannot be moved over the Internet.
“Web 3.0 is intended to increase trust,” he continues. “But right now, that’s the last thing it does. Everyone thinks it has to be based on blockchains, but that’s not true. It doesn’t have to be based on a shared ledger; instead, it has to be based on a verifiable data structure. One type of verifiable data structure is a blockchain, but I also have one: a verifiable data tree, not just a chain. So in my view, a verifiable data tree is the solution, not a shared blockchain.”
“Why is blockchain not the solution? Because you have to deal with shared governance (governance), and the latter is always a weak point. It makes for high costs and low throughput. Look at Ethereum, right now the transaction costs are bizarre! Now they’re all doing arts and crafts there to get those down with rollups. And then all these complicated systems are being implemented to protect privacy. Just try to manage zero knowledge proofs…”
The latter also has a lot to do with legal issues, such as when buying products and problems with them. Smith explains that such issues call for receipts, for a receipt. “It’s not called key event receipt infrastructure for nothing,” he says. “The basic idea is that agreements are made with receipts that are verifiable. That way, both parties have a legal recourse.”
So it all comes across as quite complex….
“Yet self sovereign identity is relatively simple. The problem is that it comes across as complex. People hear the word ‘blockchain’ and they shut down because they think it’s a big black box. With KERI, I just explained everything down to the fundamentals. Those fundamentals require a little bit of knowledge about cryptography and a little bit about software and a little bit about consensus algorithms, but it’s not remotely as complex as most blockchain systems that are supposed to provide SSI.”
Smith gets up to speed and pulls out NFTs. He mentions the complicated terms of use for the platforms you can get the NFTs from, but ultimately you can get thrown off a platform just like that. “You basically rent an NFT from such a platform, you don’t own anything. You simply don’t need a blockchain for an NFT. It’s just a chain of custody. It’s not much different than the key state. If you have an identifier and you embed it in a hash of a self certified identifier with a key state, then I can verify the origin of the NFT. After all, an NFT is nothing but an identifier. If I want to transfer ownership to someone else, I simply do a key rotation.”
And the privacy issue?
Authenticity is Smith’s number one most important component. Confidentiality follows immediately and privacy is the least important of the three in his eyes. He calls this PAC: Privacy, Authenticity and Confidentiality. You can have two of the three at a high level. According to Smith, privacy is always the weak point. It’s always difficult to keep protecting that. If you want to jump through too many hoops to do that, you make it impossible. “To protect my privacy now, that’s not that hard. To protect that information in ten years’ time is very difficult. That’s why I structurally choose strong authenticity and slightly less strong privacy protection. When I deal with people, I already lose a bit of privacy. So if I want to protect that forever, I have to go sit on an island, alone. What matters is that I don’t want to be abused by third parties. If I engage with a party, I don’t want a third party to be able to misuse my data. I share information with a party in order to do an activity together, for that party to do that, they need to know certain things about me. I have to be able to trust them and they have to trust me, very specifically for the transaction we are entering into. Now that relationship is structurally abused by third parties. Parties who don’t need to know anything about our relationship. Confidentiality is good enough to prevent third party exploitation.
The point is to be used, not to use the latest, coolest technique that is also very difficult to implement properly. That’s the principle of KERI: solve a problem in the real world with the minimum techniques needed. The dumber the technology, but still sufficient to solve the problem, the better. ‘Dumb technology’ is freely available, understandable to everyone and easy to implement. In our case: just hashes and digital signature.
With many thanks to Henk van Cann for his expertise and invaluable help in writing this article.
Biography:
The search for the ‘secret of knowing everything’ was a long pursuit of me as a child. Fortunately, in the long run you discover that it is not part of your possibilities, but it stimulates your imagination.
After doing a lot of different things, a number of activities continued to return structurally, ranging from writing texts, cooking up programmes and exhibitions and doing research. And somewhere in between all those activities, I had the opportunity to manifest myself as a science journalist at BNR, a Dutch radio station. That one time became a year and a half on a weekly basis.
Since the second decade of this century, I have manifested myself mainly as a science and technology journalist, but I also take assignments as a copywriter as long as the subjects do not overlap with my journalistic work. Most of the time, it concerns working methods in the technology sector. Apart from producing media, I take on assignments as moderator when I’m able to play a sufficient independent role. In 2018 I wrote a book on cryptocurrencies and blockchain related technologies like Bitcoin: ‘Cryptovaluta for Dummies’ or Cryptocurrencies for Dummies.
More articles!







